What is digital ad fraud?
Ad fraud is any attempt to cheat on digital advertising networks for financial gain. Since the early 2000s, various methods of ad fraud have transformed and improved, making today's ad fraud much more cunning and dodgy than before. It's important to understand what ad fraud looks like and what steps you can take to protect your ad campaigns in advance in order to avoid it.
Ad fraud usually involves fraudulent traffic (from bots as well as humans) that generates fake impressions and negatively affects CTR (click-through rate). Too much bot traffic drains ad display resources and affects publishers' efforts to build premium ad tech inventory. Non-human traffic also distorts site analytics and affects marketing campaigns. And all of this greatly affects the ad spend.
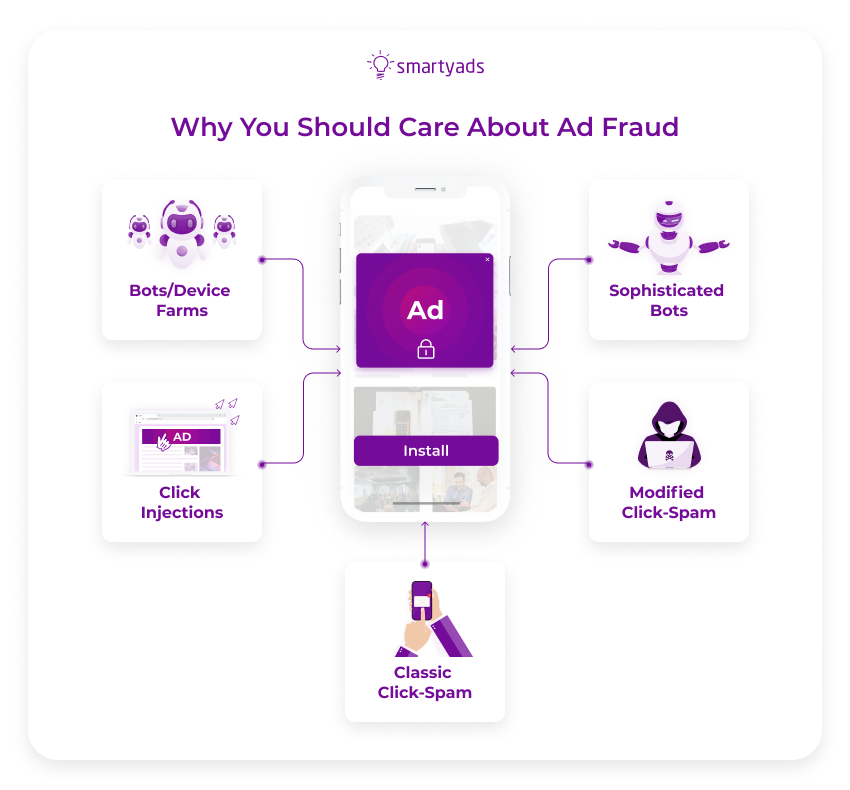
What are the types of online advertising fraud?
Source of fake traffic
Digital ad fraud has developed botnets that impersonate human traffic. This fake audience is then sold in bulk to unsuspecting publishers for a very small price.
Hidden advertising
This type of ad fraud allows ads to be shown in such a way that the user does not see them, but the system still counts them as a display. This type of advertising fraud targets ad networks that pay for impressions (views) rather than clicks.
Using this scheme, scammers create fake websites that serve as hosts on programmatic ad platforms and ad exchanges. When the ads are posted on ghost sites, bots create click fraud and generate fake impressions for which scammers get paid based on price per click (CPC) or CPM.
Domain spoofing
This type of advertising fraud presents an irrelevant low-quality site as a site with high value for programmatic media buying. To do so, ad fraud modifies advertising tags and uses ad injections. For example, an average user may unknowingly download a bad application, which can then start generating its own programming code in the user's browser and inject ads into the area of the browser the user is viewing.
Domain spoofing allows scammers to get much higher prices per thousand impressions than on an irrelevant site. The attackers then fill the low-quality site with bots and collect all advertisers' ad spend.
Click Farms/Device Farms
Click farms are usually created to scam fake ad impressions. This is one of the oldest and easiest types of ad fraud. Click farms rely on large volumes of multiple clicks. Sometimes they are done manually, and sometimes with devices programmed for this purpose. Manually, these clicks can be done by a group of people working in the same location or remotely. In 2019, one of the click farms, or device farms, was eliminated in Bangkok, Thailand.
Throwing in cookies
The average user's browser is filled with cookies. Most likely, the user won't pay attention to this because cookies are used everywhere. These cookies can even be from sites that are not advertising-related.
Once an organic or advertiser-paid purchase or display appears, there's a chance that an attribution tool or MMP platform could mistakenly attribute that paid targeted action or organic display to cookie-throwing ad fraud.
And all because there's always the possibility of a technical error or missing information. If that happens, the scammer's cookie can take advantage of that vulnerability and appropriate the attribution, and the scammer will get the money for it.
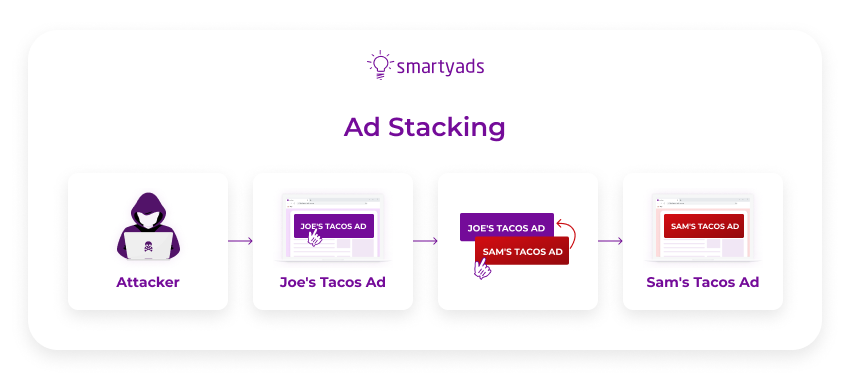
Ad stacking
Ad stacking is also known as "invisible ads" and is considered a type of display ad fraud.
Because the ads are stacked on top of each other, their audience only sees the top ad, which obscures and thus hides the banner ads below it. However, the ads below the top ad still participate in the count of impressions or views.
Reducing the size of an ad to a single pixel (pixel stuffing)
Reducing ad size to one pixel (pixel stuffing), or ad pixelization, uses an algorithm similar to ad overlay. All stacked ads get paid by the advertiser for impressions, but the audience actually sees only one.
The difference between these types of ad fraud lies in the way the ads are hidden. Unlike overlapping ads, where the ads are placed on top of each other, ad pixelation only reduces the picture of the ad to an unnoticeable size and places it inside some other ad. In this way, the ad is actually present, but people just can't notice it. This type of scam also is impression fraud.
Ad Injection
This is a type of ad fraud attack in which ads are injected into any site without the consent of the user or site owner. Such ads may be displayed in sections of the site that are not designed to display ads or may overlap another ad. For this purpose, ad fraud often uses malicious toolbars or advertising plug-ins that real users install in their browsers, unaware that they are dangerous.

Types of digital ad fraud in mobile apps
SDK spoofing
SDK spoofing, or faking, is a type of mobile ad fraud in which attackers listen for basic signals and data transmitted between mobile marketing data evaluation partners and then mimic various actions.
The signal is then reproduced along with any necessary or desired changes. Eventually, such signals are sent to the mobile marketing data evaluation partner, making all marketing analytics false.
This signal often mimics actual app installations. It can also be post-installation actions, registrations, or any other action an attacker needs. SDK spoofing is one of the most difficult forms of ad fraud to detect because it mimics human behavior very well.
Attackers can write such programs in a simple notepad and send them millions of times from ordinary home computers and inject them into MMP platforms or marketing attribution tools.
It's also dangerous because successfully spoofed SDKs can easily be replicated for all other advertising campaigns in the app using the same MMP platform.
Click Spam
In this model, the mobile ad fraud sends large volumes of fake clicks to an MMP platform or marketing attribution tool and waits for an organic installation of the app to appear. This organic installation will then be falsely attributed to that fake click and will be considered an installation that appeared due to online advertising and for which the advertiser must pay.
In such a case, the fraudster would receive the advertiser's money for that click or app installation. However, the probability of this happening is quite low, since this method of ad fraud relies on the appearance of an organic installation. Thus, this method is successful in generating a large number of clicks. We are talking about millions.
This is one of the earliest and easiest forms of ad fraud, and therefore one of the easiest for detection.
Click Injection
Click Injection is another variant of click-based ad fraud. Its purpose is to steal attribution of organic or advertiser-paid installations with the last click associated with a particular app installation. The ad fraud will simply send fake clicks to the attribution tool once the installation process has begun. In this way, the MMP platform can assume that the app install is the merit of that fake click because it was the last recorded click associated with that installation.
How do such embedded clicks get sent? There are several ways. A common way is when a malicious app or software is hidden in a real mobile device. This usually happens when a normal user downloads a seemingly normal app from the store, which actually turns out to be adware, a virus, or some other type of malware.
Bots and Emulators
Perhaps you have once used your computer to emulate Game Boy Advance to play your favorite games on a large monitor? That is, you have used an emulator. Many devices can serve as tools for ad fraud, such as bots, phones, and personal computers.
Emulators can be used to make any device look like a cell phone and plausibly simulate the installation of an application. If an app is installed on, say, a desktop computer, it's clearly an advertising scam. That's why ad fraud use emulators.
We don't necessarily need to single out such techniques or tools as a separate category, but they can be used for other types of mobile ad fraud, such as click spamming or SDK spoofing.
Device farms
Device farms are groups of devices (most often outdated iPhones and Android devices) that are programmed to install an app, then do a reset, then install the app again, and so on. Fraudsters who own such devices can be called farmers who place fraudulent devices and get a good harvest from their "plantings" in the form of illegal ad revenue (or someone's advertising budget).
Considering that there are more phones than people today, they definitely represent an opportunity to easily get hold of such online ad fraud tools and create a large farm of devices.

How do you recognize a malicious app, plug-in, or adware?
The average user can, unsuspectingly, download an ad fraud app/plug-in. Examples of such applications include something with few functions, like a notepad or a flashlight. And examples of such plug-ins include a plug-in for checking grammar, a plug-in for creating screenshots, and a plug-in for displaying the time in different time zones. Such malicious applications usually perform their stated functions, thus not arousing suspicion in the average user.
In addition, the developers of such apps usually buy fake reviews. Thus, one of the typical warning signs of a malicious app is many reviews with one or five stars. Such scores do not conform to the normal distribution model and are considered signs of fake reviews. You can also read the reviews yourself to see if they look plausible. Fake reviews are usually sparse on details or full of nothing but praise without highlighting specific benefits. Also, pay attention to one-star reviews. If many reviews contradict the five-star reviews, this also indicates that you are facing a potentially dangerous plug-in or app.
Try to install and download plug-ins and apps only from trustworthy sources. Look at other applications from the same developers. Many attackers develop a large number of simple apps or plug-ins that are not thematically related.
Another sign of malicious apps is that the apps don't work. If the feedback says that the app is simply useless and does not perform its functions, this is a clear signal that the app is malicious. Unfortunately, once installed, many malicious apps and plug-ins take advantage of their built-in anti-removal capabilities. In addition, these malicious apps often drain your device's battery level due to additional hidden functions that are constantly running in the background.
How to prevent ad fraud for your business
- Hire a data processing and analysis specialist to help with advertising fraud detection;
- Analyze your business data. Does your revenue match your MMP platform data?;
- Always double-check your marketing data;
- Use only large, verified advertising platforms with high-quality ad tech inventory;
- Read our guide on Ad Fraud Detection Tools.
To sum it up
Fraudsters exist in every sphere of our life and online advertising, unfortunately, is no exception. In this article, we described the most famous ad fraud schemes, but day by day there are new ways to trick advertisers and publishers. Therefore, the main rule for any business or advertising platform will always be "use only proven programmatic advertising platforms" for preventing ad fraud.
Only fraud-free traffic on SmartyAds DSP! Join in.


.webp)